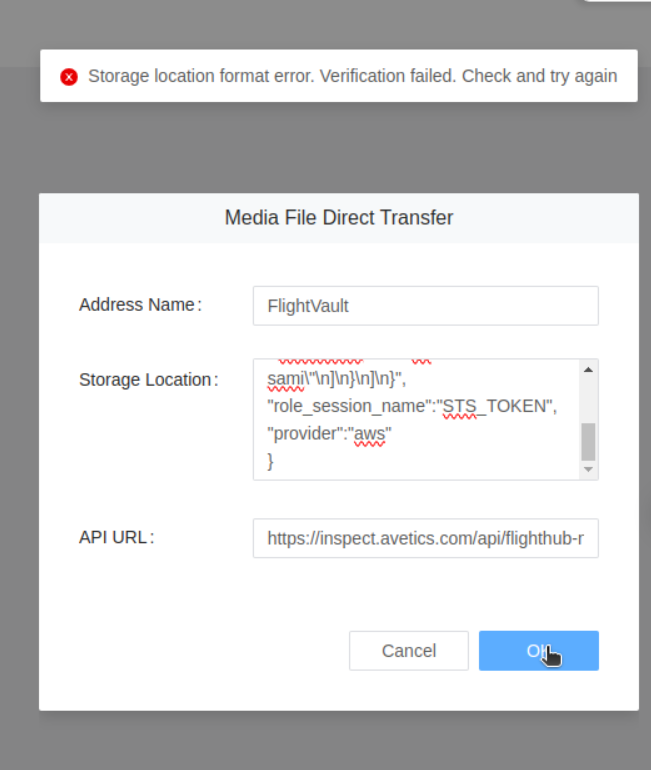
Facing Error - Storage location format error. Verification failed. Check and try again
CompletedDetails of the Error i am facing:
I am trying to add a third party cloud service in flight Hub DJI and facing error which says “Storage location format error. Verification Failed. Check and Try again”
Here is my storage Location Format of the objects that i have passed:
First one:
{
"access_key_id":"XXXXXXXXXXXXXXXXXX",
"access_key_secret":"XXXXXXXXXXXXXXXXXX",
"bucket":"XXXXXXXXX",
"region":"XX-XX-1",
"arn":"arn:aws:iam::XXXXXXXXX:role/XXXXXX",
"policy":"{\n\"Version\": \"1012-10-17\",\n\"Statement\": [\n{\n\"Sid\":\"VisualEditor0\",\n\"Effect\": \"Allow\",\n\"Action\": [\n\"s3:PutObject\",\n\"s3:GetEncryptionConfiguration\",\n\"s3:GetBucketLocation\",\n\"s3:PutObjectAcl\"\n],\n\"Resource\": [\n\"arn:aws:s3:::*/\",\n \"arn:aws:s3:::XXXXXXXXX\"\n]\n}\n]\n}",
"role_session_name":"STS_TOKEN",
"provider":"aws"
}
Second One:
{
"access_key_id": "XXXXXXXXXXXXXXXXXX",
"access_key_secret": "XXXXXXXXXXXXXXXXXX",
"bucket": "XXXXXXXXX",
"region": "XX-XX-1",
"arn": "arn:aws:iam::XXXXXXXXX:role/XXXXXX",
"policy": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::XXXXXXXXX:role/XXXXXX"
}
]
},
"role_session_name": "STS_TOKEN",
"provider": "aws"
}
Third one:
{\n \"access_key_id\": \"XXXXXXXXXXXX\",\n \"access_key_secret\": \"XXXXXXXXXXXXXXXXXX\",\n \"bucket\": \"XXXXXXXXX\",\n \"region\": \"XX-XX-1\",\n \"arn\": \"arn:aws:iam::XXXXXXXXX:role/XXXXXX\",\n \"policy\": {\n \"Version\": \"2012-10-17\",\n \"Statement\": [\n {\n \"Effect\": \"Allow\",\n \"Action\": \"sts:AssumeRole\",\n \"Resource\": \"arn:aws:iam::XXXXXXXXX:role/XXXXXX\"\n }\n ]\n },\n \"role_session_name\": \"STS_TOKEN\",\n \"role_session_token\": \"STS_TOKEN\",\n \"provider\": \"aws\"\n}
Below is the screenshots annexed:
Storage_Location_Format_Error:
Request:
-
The storage information in the following format is correct. Additionally, it's recommended that you use AWS's SDK to test whether your configuration details are accurate. {"access_key_id":"XXXXXXXXXXXXXXXXXX","access_key_secret":"XXXXXXXXXXXXXXXXXX","bucket":"XXXXXXXXX","region":"XX-XX-1","arn":"arn:aws:iam::XXXXXXXXX:role/XXXXXX","policy":"{\n\"Version\": \"1012-10-17\",\n\"Statement\":[\n{\n\"Sid\":\"VisualEditor0\",\n\"Effect\": \"Allow\",\n\"Action\":[\n\"s3:PutObject\",\n\"s3:GetEncryptionConfiguration\",\n\"s3:GetBucketLocation\",\n\"s3:PutObjectAcl\"\n],\n\"Resource\":[\n\"arn:aws:s3:::*/\",\n \"arn:aws:s3:::XXXXXXXXX\"\n]\n}\n]\n}","role_session_name":"STS_TOKEN","provider":"aws"} -
Also, you can go ahead and conduct the test without filling in the policy field. Just like the following: { "access_key_id":"XXXXXXXXXXXXXXXXXX", "access_key_secret":"XXXXXXXXXXXXXXXXXX", "bucket":"XXXXXXXXX", "region":"XX-XX-1", "arn":"arn:aws:iam::XXXXXXXXX:role/XXXXXX", "role_session_name":"STS_TOKEN", "provider":"aws" } -
Also, you can go ahead and conduct the test without filling in the policy field. Just like the following: { "access_key_id":"XXXXXXXXXXXXXXXXXX", "access_key_secret":"XXXXXXXXXXXXXXXXXX", "bucket":"XXXXXXXXX", "region":"XX-XX-1", "arn":"arn:aws:iam::XXXXXXXXX:role/XXXXXX", "role_session_name":"STS_TOKEN", "provider":"aws" }
Please sign in to leave a comment.
Comments
4 comments